Best cybersecurity solutions for small businesses 2025
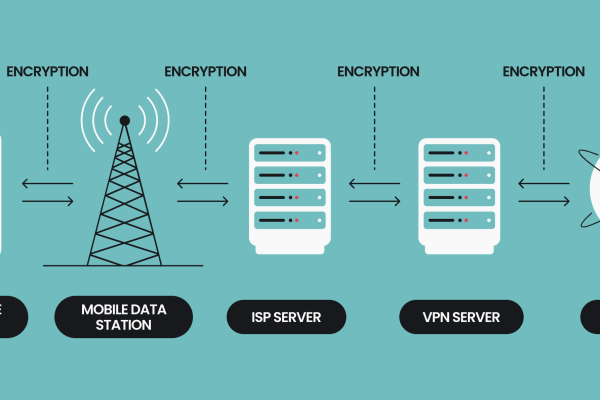
Small businesses increasingly face sophisticated cyber threats, making cybersecurity a top priority in 2025. Unlike large enterprises, small businesses often lack dedicated IT teams, so choosing effective, easy-to-manage security solutions is critical to protect sensitive data and maintain customer trust. Key Cybersecurity Needs for Small Businesses Top Cybersecurity Solutions for 2025 Choosing the Right Solution…